Task 1 - Familiarize yourself with the HCL syntax used in Terraform
Learn about HCL blocks, parameters, and arguments
🛑 HCL blocks
HCL (HashiCorp Configuration Language) is a domain-specific language (DSL) used in Terraform to define and configure infrastructure resources. HCL files typically have a .tf extension and contain the configuration for a Terraform project. HCL uses blocks to define resources. Within each block, you can specify attributes and their corresponding values to configure the desired behavior of the resource.
A block is a container for other content. Blocks have a type that can have zero or more required labels followed by { } brackets that contain the block's body. Blocks can be nested inside each other. This a general representation of a block
type "label_1" "label_2" {
argument_1 = value_1
argument_2 = value_2
}
There are several block types used to define different aspects of infrastructure configuration.
Provider Block
Specifies the cloud or service provider that Terraform will interact with.
Contains configuration settings such as access credentials and API endpoints.
Resource Block
Defines a specific infrastructure resource that Terraform will manage.
Specifies the resource type, such as EC2 instances, S3 buckets, or VPCs. Contains attributes that configure the behavior and properties of the resource.
Data Block
Retrieves and imports data from an external source into the Terraform configuration.
Allows you to query and fetch information to use in resource configurations. Typically used to gather information about existing infrastructure resources.
Variable Block
Declares input variables that can be passed into the Terraform configuration.
Specifies the variable name, type, default value, and other optional properties. Enables parameterization and dynamic configuration of the infrastructure.
Output Block
Defines values that Terraform will display as outputs after successful resource provisioning.
Allows you to expose information from the infrastructure for use by other systems or modules. Specifies the output name and the value to be displayed.
Module Block
Encapsulates a reusable set of Terraform configurations into a single module.
Defines input variables and output values specific to the module. It enables code reuse and modularity by grouping related resources and configurations.
Provisioner Block
Specifies actions to be taken on a resource after it is created or updated.
Allows for running scripts or executing commands on the resource. It is commonly used for tasks like initialization, configuration, or software installation.
Locals Block
Declares local values or expressions that can be used within the Terraform configuration.
Enables the creation of intermediate variables or complex expressions for reuse.
Terraform Block
Contains global configuration settings for Terraform itself and includes backend configuration, required provider versions, and other global settings.
Allows you to configure how Terraform behaves during the execution of the configuration.
🛑 Parameters
Parameters are variables that are defined within HCL blocks.
They allow you to provide inputs or configurations to control the behavior of resources or other components.
Parameters are defined using the
parameter_name = valuesyntax within block declarations.Parameters can be assigned default values or marked as optional using default values or null.
🛑 Arguments
Arguments are the specific values assigned to the parameters within HCL blocks.
They provide concrete values to the parameters and influence the behavior of resources or components.
Arguments are passed in key-value pairs to configure attributes within a block.
Arguments can be static values or interpolated expressions that reference other variables or data.
Explore the different types of resources and data sources available in Terraform
🛑 Resources
Resources are the most important part of Terraform. Resources are defined by resource blocks. A resource can define one or more infrastructure resource objects, such as VPCs, virtual machines, or DNS records, key-value pair data, etc.
resource "aws_instance" "web_server" {
ami = "ami-a1b2c3d4"
instance_type = "t2.micro"
}
🛑 Types of resources
Compute Resources:
Instances: Virtual machines or server instances, such as AWS EC2 instances, Google Compute Engine instances, or Azure virtual machines.
Containers: Container resources, like AWS ECS tasks, Kubernetes pods, or Azure Container Instances.
Serverless Functions: Resources for serverless computing, such as AWS Lambda functions, Google Cloud Functions, or Azure Functions.
Networking Resources:
Virtual Networks: Network components like virtual private clouds (VPCs), subnets, and routing tables, such as AWS VPC, Google VPC, or Azure VNet.
Load Balancers: Resources for load balancing traffic, like AWS ELB/ALB/NLB, Google Load Balancer, or Azure Load Balancer.
DNS: Domain Name System resources, such as AWS Route 53, Google Cloud DNS, or Azure DNS.
Storage Resources:
Block Storage: Resources for block-level storage, such as AWS EBS volumes, Google Persistent Disks, or Azure Managed Disks.
Object Storage: Resources for object storage, like AWS S3 buckets, Google Cloud Storage buckets, or Azure Blob Storage.
File Storage: Resources for file storage, such as AWS EFS, Google Cloud Filestore, or Azure Files.
Database Resources:
Relational Databases: Managed relational databases, like AWS RDS, Google Cloud SQL, or Azure Database for MySQL/PostgreSQL/SQL Server.
NoSQL Databases: Managed NoSQL databases, such as AWS DynamoDB, Google Cloud Firestore, or Azure Cosmos DB.
Data Warehouses: Resources for data warehousing, like AWS Redshift, Google BigQuery, or Azure Synapse Analytics.
Security Resources:
Identity and Access Management: Resources for managing identities, permissions, and access control, such as AWS IAM, Google Cloud IAM, or Azure AD.
Encryption and Key Management: Resources for encryption and key management, like AWS KMS, Google Cloud KMS, or Azure Key Vault.
Security Groups: Resources for network security groups or firewalls, such as AWS Security Groups, Google VPC Firewall Rules, or Azure Network Security Groups.
Data Sources
Data sources provide dynamic information about entities that are not managed by the current Terraform and configuration.
Variables provide static information.
Referencing a resource defined in a data source won’t create the resource itself, and your plan will fail if you reference nonexistent data or infrastructure.
Data sources allow data to be fetched or computed for use elsewhere in Terraform configuration.
External data sources must return information in JSON format.
Types of Data Sources
Infrastructure Data Sources
"aws_vpc" - Retrieves information about an existing Amazon VPC.
"google_compute_network" - Retrieves information about a Google Cloud VPC network.
"azurerm_subnet" - Retrieves information about an Azure subnet.
Cloud Service Data Sources
"aws_s3_bucket" - Retrieves information about an existing Amazon S3 bucket.
"google_storage_bucket" - Retrieves information about a Google Cloud Storage bucket.
"azurerm_cosmosdb_account" - Retrieves information about an Azure Cosmos DB account.
DNS Data Sources
"aws_route53_zone" - Retrieves information about an Amazon Route 53 DNS zone.
"google_dns_managed_zone" - Retrieves information about a Google Cloud DNS managed zone.
"azurerm_dns_zone" - Retrieves information about an Azure DNS zone.
Security Data Sources
"aws_iam_policy" - Retrieves information about an AWS IAM policy.
"google_service_account" - Retrieves information about a Google Cloud service account.
"azurerm_key_vault" - Retrieves information about an Azure Key Vault.
Database Data Sources
"aws_db_instance" - Retrieves information about an Amazon RDS database instance.
"google_sql_database_instance" - Retrieves information about a Google Cloud SQL database instance.
"azurerm_mariadb_server" - Retrieves information about an Azure Database for MariaDB server.
Task 2 - Understand variables, data types, and expressions in HCL
Create a
variables.tffile and define a variable
Create a file named
variables.tfand open it in a text editor.In the
variables.tffile, define a variable using the Terraform syntax.variable "file_name" { type = string default = "demo-file.txt" }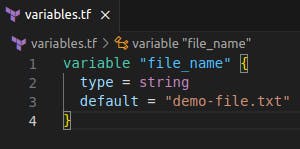
Use the variable in a main.tf file to create a "local_file" resource
In the
main.tffile, we can now use thelocal_fileresource to create a file and set its file name using the defined variable.resource "local_file" "demofile" { filename = var.file_name content = "Hey, this is shreya and I'm doing terraweek challenge" }
Open a terminal or command prompt, navigate to the directory where your Terraform files are located.
Run
terraform initcommand to initialize the Terraform configuration and download the necessary providers. Runterrafrom validateto validate the files.
Run
terraform planto check the plan and then runterraform applycommand to create thelocal_fileresource based on the defined variable. Terraform will prompt you to confirm the creation of the resource. If you're satisfied with the changes, typeyesand press Enter to proceed.
Thus, a file is created with content.

Task 3 - Practice writing Terraform configurations using HCL syntax
Add required_providers to your configuration, such as Docker or AWS
Open the
main.tffile in a text editor.Add the
required_providersblock at the top of the file to specify the providers you need.
Test your configuration using the Terraform CLI and make any necessary adjustments
Run the
terraform initcommand to initialize the Terraform configuration and download the necessary providers. This command will detect therequired_providersblock in themain.tffile and download the Docker provider.Run the
terraform plancommand to preview the changes that Terraform will apply.If the plan looks good, run the
terraform applycommand to apply the changes and create the resources.
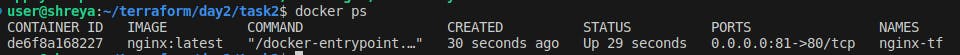
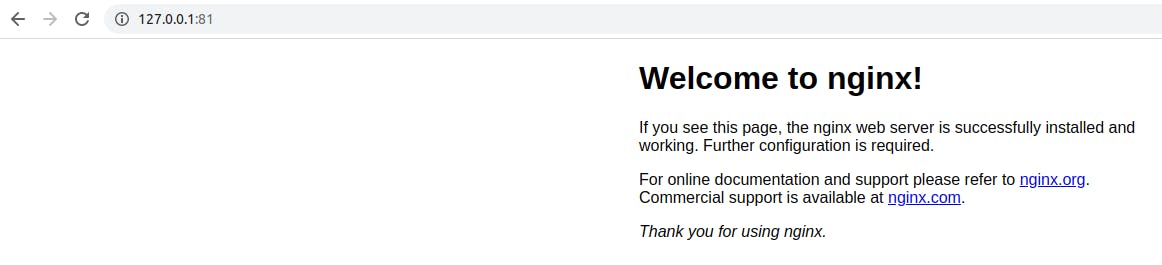
Check whether the docker container is running or not.
Thank you for reading!!
~Shreya Gupta
Great initiative by the #trainwithshubham community. Thank you Shubham Londhe
#devops #terraweek #terraform #hcl #terraformconfigurationlanguage